TABLE OF CONTENTS
- First Steps
- Replicated Panel Configuration
- IAM Migration Endpoint Enabled
- Setting OTP (One-time Password) Enabled
- Setting OTP (One-time Password) after registration Enabled (sign up)
- Expose IAM Admin Resources
- Login Mode for IAM
- Username/Password & SSO
- LDAP
- Duplicate email
- Show IAM Admin Username
- IAM Admin Password
- Password strength policy
- IAM/Products Secrets
- Brute Force Protection
- Resources
- First installation guideline
Introduction
In this guide, you will find all the relevant information on how to configure your Identity and Access Management (IAM) system into a new on-premises environment.
This covers the IAM configuration on the Replicated Panel as well as the Single Sign-On configuration, also considering the cases where data migration is necessary.
First Steps
At this point, you should already have the Kubernetes Cluster installed and configured and are able to access the Replicated Panel, similar to the screenshots below. The configuration includes certificates, domain, and SMTP servers (not included in this guide).
Here you can find the IAM configuration fields, their explanation, and the suggested default values.

Once logged in, you see the following view. Click Config to edit the latest version.

Navigate to the paragraph “Identity & Access Management Configuration.” Here you find a brief explanation of these fields:

Replicated Panel Configuration
See below the configuration options explained in detail.
In case there are no questions about these, please follow up on the First Installation Guideline.
IAM Migration Endpoint Enabled
Should be enabled only when existing Labfolder or Laboperator users are being migrated to IAM.
Initially, this parameter should be disabled.
For further details, please see the chapter Migrating Users to IAM
Setting OTP (One-time Password) Enabled
One-time Password is the terminology for Multi-Factor Authentication. Enabling this option allows the users to enable MFA on their profile page if they are logged in with email and password.
For users logged in with Single Sign On, there is no Multi-Factor Authentication, as the user authentication is under the responsibility of the identity provider (e.g. Google or Microsoft).
For more details about MFA, please see our blog post about it: Labforward - Add an additional layer of security by enabling two-factor authentication on your Labforward account.
Setting OTP (One-time Password) after registration Enabled (sign up)
With this option enabled, all users are required to set up their MFA devices during the registration step.
Expose IAM Admin Resources
This parameter means “exposing IAM administration panel together with the application.”
In case your application is deployed in an internal network, this can be kept always enabled. Otherwise, the recommendation is to enable it only for configuration/administration work with the users' administrative data, for example, blocking or unblocking a user or changing their credentials (superuser tasks).
Login Mode for IAM
Username/Password & SSO
This option should be used if the users need to access the applications with credentials or with Google, Azure, or Shibboleth. By selecting this option, further configurations are still needed in IAM Admin Panel to configure the SSO provider.
The next three options are enabled as a subset of this one.
Allow Only SSO Login
Users are not allowed to sign up or log in with email and password, only with SSO (useful to restrict users to specific domains).
Disable Editing of User Identity Fields
Users are not allowed to modify their first and last names on the profile page. This information is always synchronized with the identity provider.
User Can Disconnect Their SSO account
When enabled, users can revert their identity provider configuration to the typical email/password method.
LDAP
This option should be enabled in case your users are controlled under an LDAP server. By selecting this option, further configurations are still needed in IAM Admin Panel to configure the LDAP server.
For LDAP configuration, please see LDAP Configuration
Duplicate email
This option should be enabled only on very specific scenarios where, having a specific SSO configuration, the same user has two different accounts and these accounts have identical email addresses. In this case, the user is not identified by their email but by the internal SSO provider identifier. We recommend enabling this option only when suggested by the Labforward identity specialists.
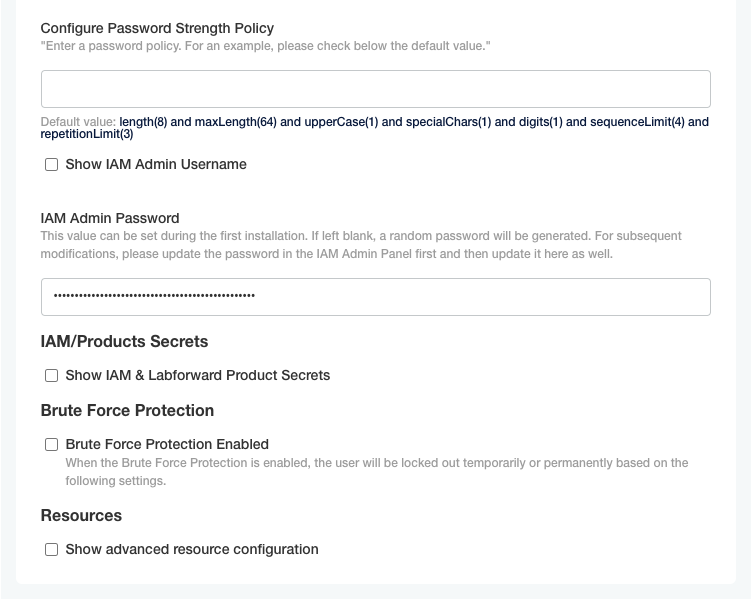
Show IAM Admin Username
This checkbox reveals the username to be used to login into the IAM Admin Panel and perform administrative actions with the registered users.
IAM Admin Password
This value should be set only before deploying the application for the first time and describes the password for the administrator user.
Please see section First installation guideline for more details about this field.
Password strength policy
Determines how strong should be the user password during configuration time. The recommendation is to keep the default value.
It means the password should have at least 8 characters, not more than 64 characters, should have one upper case letter, one special character, one numerical digit, no sequence of 4 or more characters (abcd, for example), and not 3 or more repeated characters (aaa, for example).
IAM/Products Secrets
Should be disabled and used only during maintenance with Labforward identity specialists.
Brute Force Protection
Enabling this option allows IAM to detect when a possible attacker tries to brute-force a user account by guessing their password.
With this option enabled, depending on the configuration of the parameter Failure Factor below, there is a chance of false-positive and users being temporarily or permanently disabled in the application.
Permanent Lockout Enabled
When a user is locked, only an administrator can re-enable their account. Otherwise, it’ll be unlocked in some time.
The time to unlock the user is incremental so, for example, the first time the account is locked the user needs to wait 1 minute. After that, every new lock increases 1 minute to the time, consequently.
Minimum Quick Login Wait Seconds
Time a user will be disabled if they log in faster than Quick Login Check Milliseconds.
Quick Login Check Seconds
Minimum time between login attempts.
Failure Factor
The maximum number of login failures permitted.
Resources
Advanced Kubernetes resources configuration. It should be modified only by Labforward specialists.
First installation guideline
In order to execute the installation in steps, the suggestion is to configure a basic version of IAM initially and, later then, fine-tune it.
Before having deployed IAM for the first time, the field IAM Admin Password needs to be set.
Please set this value if and only if the IAM application hasn’t been deployed yet.

Save the configurations and deploy the application.
After the initial deployment, the following result is expected to be seen after kubectl get pod command:
In order to verify the application, please access the following:
The following login page should be visible:

If the environment variables for SMTP are correctly configured, account creation should be possible, and the applications should be accessible from the Apps menu in the logged-in space.
With that, the initial step is completed.
In the next chapters, the Administration Panel, Identity Providers, and Data Migration will be covered.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article